How does SSL works ?
Hello, This is Shahper a tech savvy who explores new things and loves to share with the world :)
What is SSL?
If you are little bit familiar with “system designing” or “networking” concepts you would have known this term, “SSL” stands for “Secure Socket Layer”
A google search for definition of SSL do the task for me:
Secure Sockets Layer (SSL) is a protocol that establishes a secure connection between two devices or applications on a network.
What was the need of SSL ?
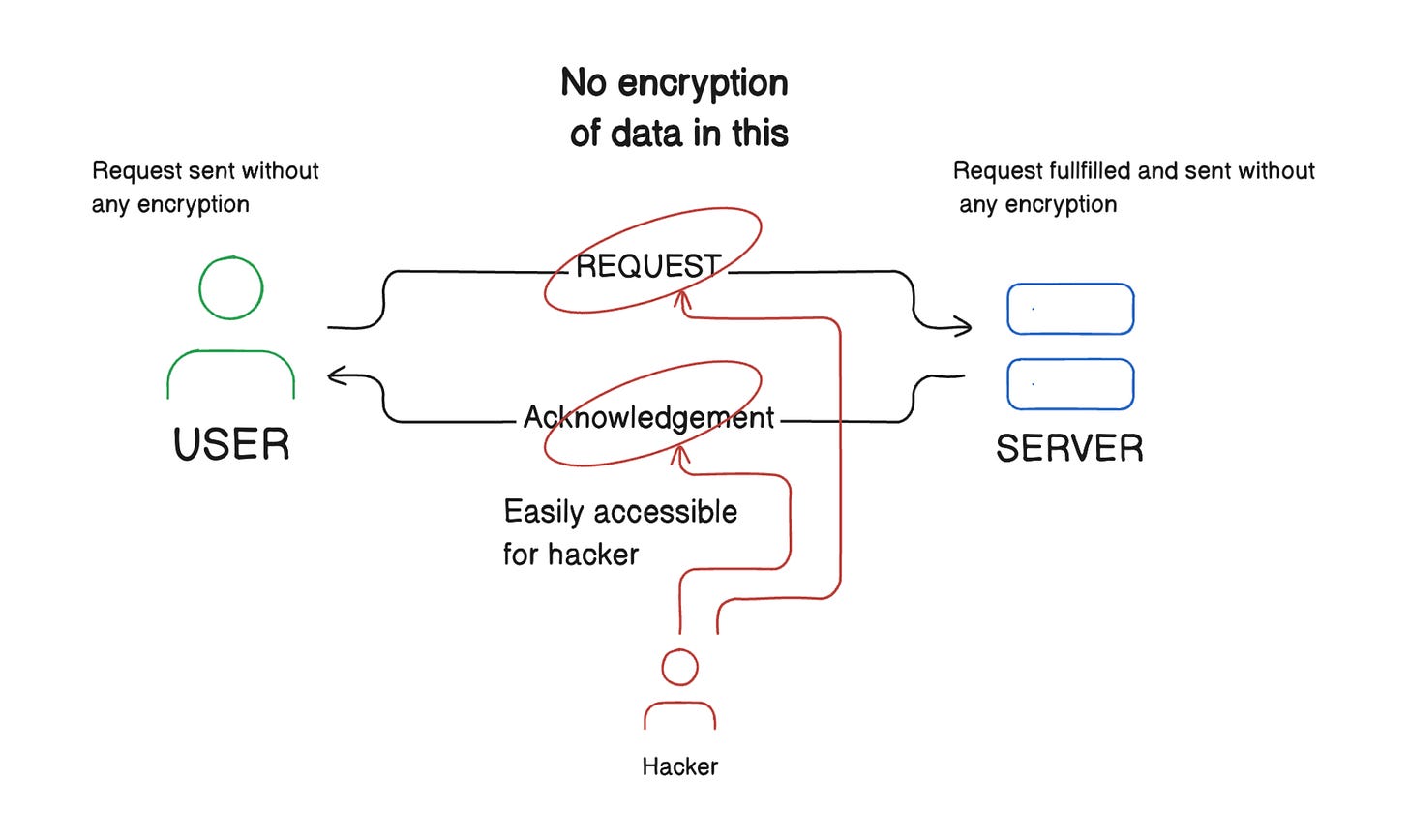
Before SSL, users communicated and made requests to servers, but during the transmission of these requests and responses, it was common for hackers or unauthorized individuals to intercept and exploit the information in the data packets.
To address this issue, cryptography was introduced, which involves the encryption and decryption of data. However, this approach faced a problem: while encryption and decryption require public and private keys, there was the challenge of securely sharing these keys.
It is important to note: "The public key is used to encrypt the data, and the encrypted data can only be decrypted by the private key."
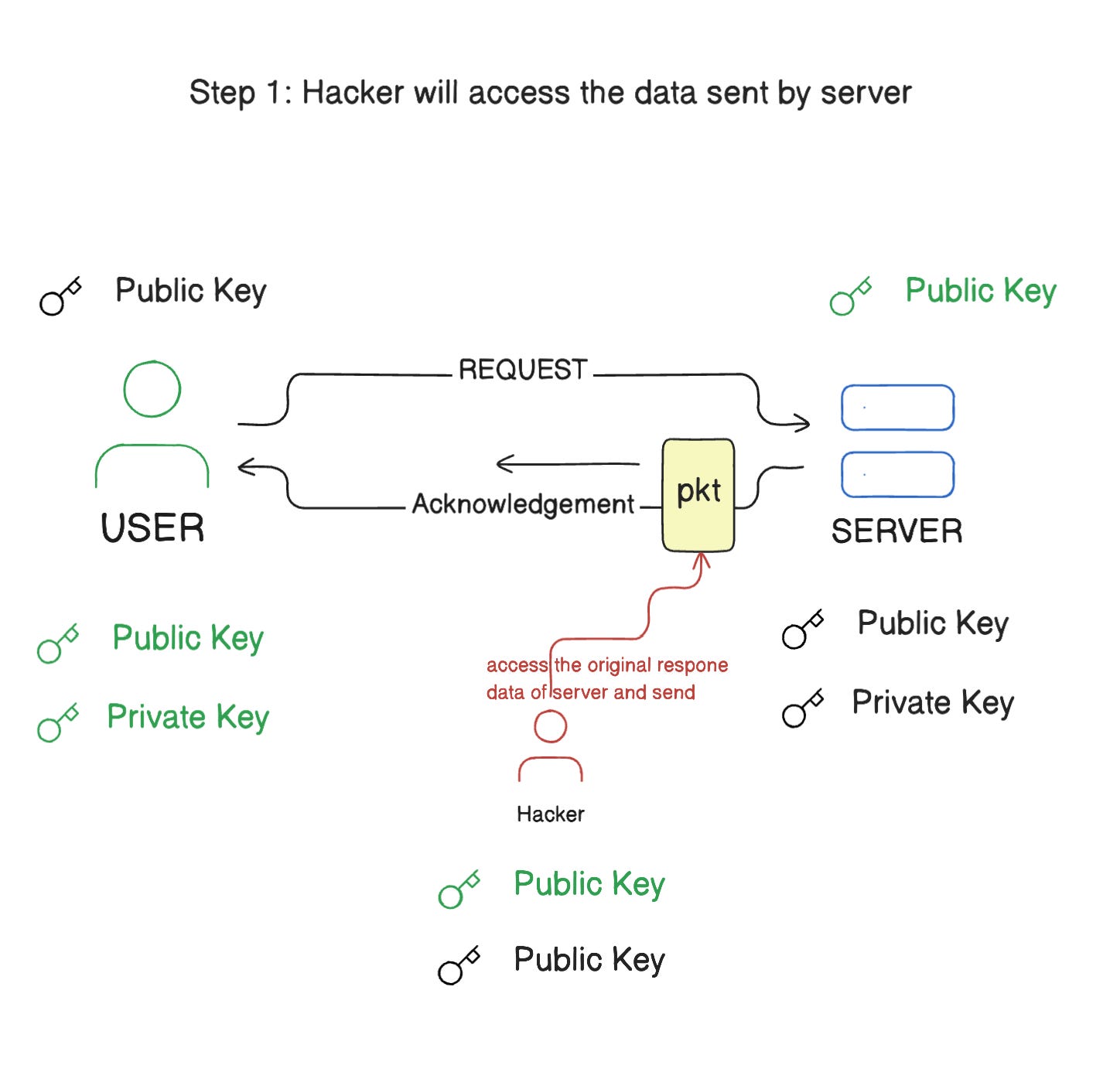
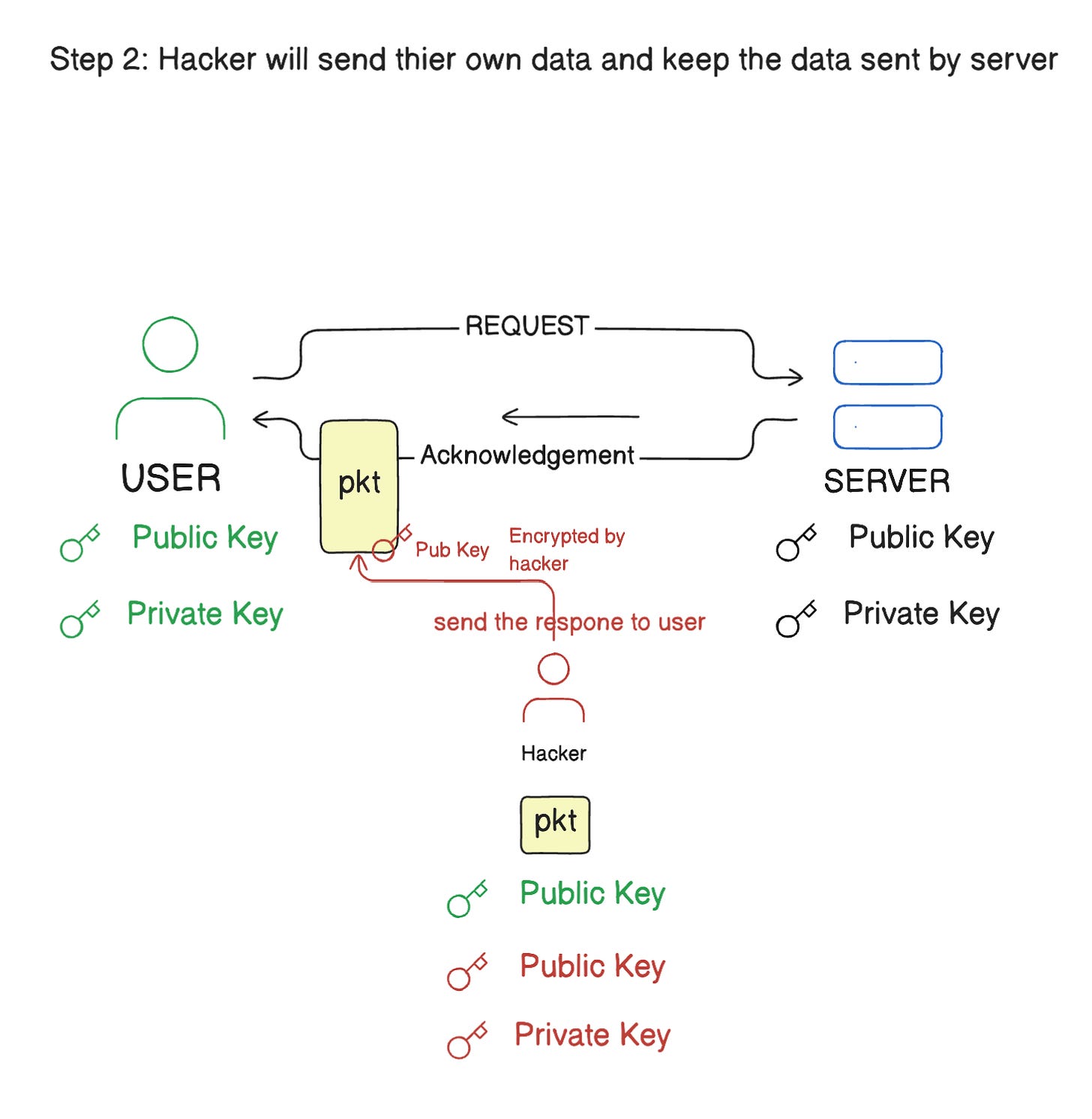
What happened here is that, when a request is sent by the client, it is encrypted with the client's public key and can only be decrypted by the corresponding private key. In this scenario, an unauthorized system intercepted the request and obtained a copy of the client’s public key. When the server acknowledges the request and sends a response, the unauthorized system intercepts the response, obtains the server's public key, and replaces it with its own public key before sending the response packet to the client. By doing this, the unauthorized system acts as an intermediary between the client and server, accessing, forwarding, and even manipulating the data.
To address the question of how to share keys securely, one solution might be the "in-person exchange of the key," but this is impractical.
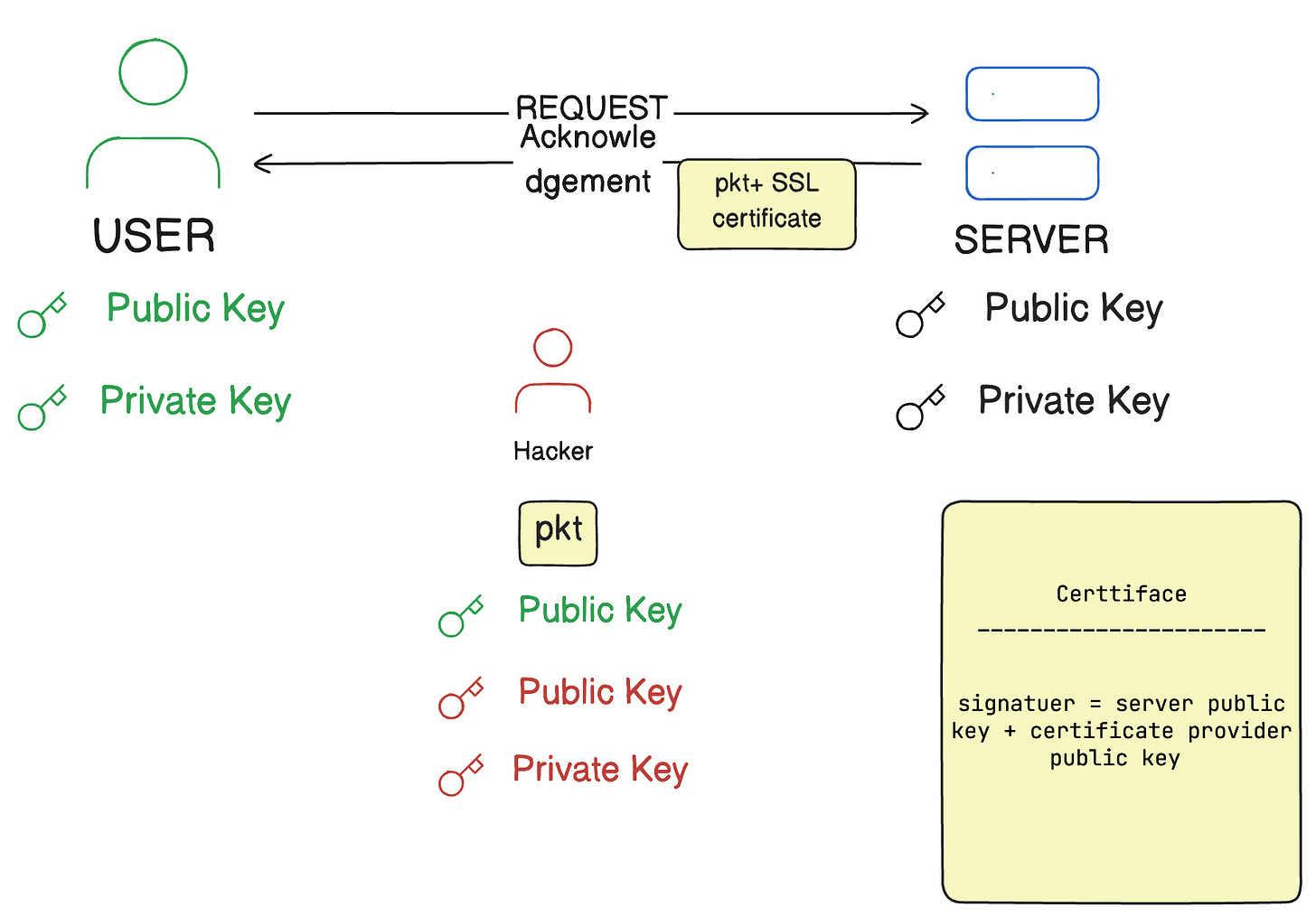
Let's understand how SSL and SSL Certificates solve this problem. Secure Sockets Layer (SSL) is a protocol that establishes a secure connection between two devices or applications on a network. When a connection is established, SSL generates certificates to verify the legitimacy of the parties involved in data exchange.
These certificates are issued by a Certificate Authority (CA), such as Let's Encrypt. A key feature of these certificates is the digital signature, which is used to verify the legitimacy of the sender or receiver. An SSL certificate contains several pieces of information, but two key components are:
The name of the certificate holder.
The signature on the certificate.
The certificate signature includes:
The public key of the certificate holder.
The public key of the certificate issuer (e.g., Let's Encrypt's public key).
This system helps the user or client identify the legitimacy of a packet, as the signature on the certificate allows for verification of the sender's identity.
Here, even if a third-party user sends an untrusted data packet, it can easily be detected by the certificate, as the certificate contains the public key of the certificate provider and the public key of the server. This ensures that the data being transmitted is secure and legitimate.
good to know stuff:
A Certificate Authority (CA) generates and issues SSL certificates after a vetting process called validation.
Some most famous and reliable CA’s (Certificate Authority) are DigiCert, Certificate Authority,RapidSSL Certificate Authority and many more are there
SSL and SSL Certificates play a crucial role in ensuring secure communication over networks. By encrypting data and verifying the legitimacy of parties involved in data exchange, SSL protects against unauthorized access and manipulation, providing a secure environment for users and servers to interact.
Stay tuned for more insightful content on technology and networking concepts!!!
Find Me : | X : shahpershahin | | LinkedIn: shahpershahin | |GitHub: shahpershahin |